-
Information security risk management framework
The company has established a dedicated department for information security, the "Information Security Management Department", at the support center, with information security managers and responsible personnel. Their responsibility is to formulate information security policies and management methods, and refer to ISO 27001, CNS 27001 information security management system standards, implement management methods, continuously improve and eliminate deficiencies, to ensure that policies and management methods are effectively implemented; relevant implementation results are regularly reported to the company's senior meetings to reduce operational risks.
The Information Security Management Department maintains the confidentiality, integrity, availability and legality of the company's information and communication, and prevents the risks of human negligence, intentional damage and natural disasters, avoiding improper use, leakage, tampering, damage, disappearance, etc. of information and communication and information assets, affecting the company's operations and causing damage to the company's interests. For this purpose, the Information Security Management Department regularly conducts information security inspections and submits inspection reports to the responsible supervisors for review; and understands, tracks and reviews the improvement of the findings and problems raised by the inspection, to confirm that the internal and external related personnel and units all follow the company's information and communication security policies and information security management methods. -
Information and communication security policy
• Implement information security management methods
• Avoid using unauthorized illegal software
• Ensure that information and communication equipment and backups operate normally every day
• Backup completely, ensure disaster recovery and database restoration
• Log in and out of the computer room control records in detail, protect the physical security of the computer room
• In order to implement the employees' compliance with information security regulations, all personnel must sign the information security commitment letter
• In order to ensure strict control of information and communication equipment, we will implement computer room equipment abnormal records and computer room equipment list
• Establish a rigorous disaster recovery process, ensure the timeliness of information and communication service recovery
• Implement information requirements application, review various information operations
• Conduct network group control, distinguish between internal and external network policies, limit access scope
• Strict account separation management, control authorized access
• Complete data destruction operation records, prevent the company's sensitive information from leaking
• Join the information security information sharing and analysis organization, grasp the information security threats and weaknesses, prevent and respond in advance
• Regularly hold employee information and communication security education and training, enhance the information security awareness of all staff
-
Specific Management Plan
To achieve information security policy and objectives, establish comprehensive and complete information security protection, and implement information security management matters and specific management plans based on the following contents:
• Use next-generation firewall and introduce international intelligence protection database for joint defense, produce network attack event report every day, to provide information security responsible personnel with timely response measures.
• Choose international software giant's email service system, guarantee 99.99% service availability, and work with protection module, to protect email and collaboration, avoid zero-day malicious code, phishing and business email leakage risk.
• Install advanced MDR anti-hacking software on information host and computer, and entrust vendor to monitor and protect 24 hours, produce information security report every month, review recent information security events with information security partner vendor every quarter.
• In addition to regular backup, information service performs disaster recovery drill for core information service every year, to strengthen information security responsible personnel's disposal ability after encountering natural or man-made disaster.
• Perform account separation management according to personnel's job responsibility, special privilege must be applied for approval and backup, and regularly change personnel account password, require password complexity, to reduce risk.
• Regularly conduct information security education and training, to enhance personnel's information security awareness.
• Join TW-ISAC computer network crisis handling and coordination center's information security intelligence sharing organization, obtain information security early warning intelligence, information security threat and weakness information.
-
Resources for Information Security Management
Information security has become an important issue for the company's operation, and the corresponding information security management matters and resource allocation plan are as follows:
• Dedicated personnel: The "Information Security Management Department" of the company's organization is responsible for information security, with one full-time information security manager and one information security staff, who are in charge of the company's information security planning, emergency response, incident handling, technology introduction and audit, to maintain and continuously strengthen information security, and complete the information security dedicated personnel declaration for listed companies.
• Information security organization structure:
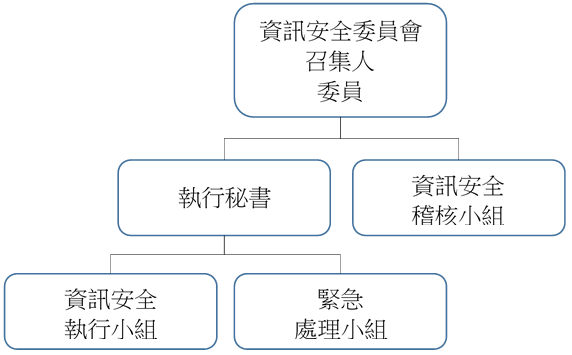
Customer satisfaction: No major information security incidents, no complaints of customer data loss.
Signing information security commitment: All employees and new employees have completed signing the information security commitment.
Information security announcement: One information security promotion was issued this year, conveying the relevant regulations and precautions for information security protection.
Using the company's online learning platform and new employee orientation, comprehensive information security related education and training are implemented, and the total learning hours in 2025 reached 73 hours.
- Ma Wei
- Tel: +886-3-6676868
- Fax: +886-3-6676869
- Email: IR@novatech.com.tw
- Ou Junyan
- Tel: +886-3-6676868
- Fax: +886-3-6676869
- Email: IR@novatech.com.tw
- KGI Securities
- 5F., No. 2, Chung Ching South Road, Section 1, Taipei, Taiwan, ROC
- Tel: +886-2-23892999
- Fax: +886-2-23891878
