The Information Security Department ensures the confidentiality, integrity, availability, and legal compliance of the Company's information and communications to
prevent improper use, leakage, tampering, damage, or loss of information and communication assets due to human error, intentional destruction, or natural disasters, which could disrupt operations and harm company interests.
Therefore, regular information security inspections are conducted, and inspection reports are submitted to responsible supervisors for review. The findings and issues identified during inspections are understood, tracked, and reviewed for improvement to ensure that all internal and external personnel and units comply with the Information Security Policies and Objectives and Information Security Management Methods.
Information Security Management ┃ Management Approach
Significance and Meaning to the Company
- Information security is related to all operational and financial information of the Company, as well as customer and personal information, directly affecting the Company's reputation and trust with customers and partners.
Management Strategies
-
Establish information security-related methods and operational rules such as Information Security Policies and Objectives, Information Security Management Methods,and Information Security Emergency Event Management Regulations, continue security-related verification and regularly implement various crisis drills, strengthen employee information security education and training, and enhance information security risk defense capabilities.
- Strengthen information security awareness and knowledge among all employees and enhance the information security architecture to comply with regulations and meet customer needs.
Policy/Commitment
-
Strengthen information security management, establish a secure and reliable information operating environment, and ensure the security of data, systems, equipment and networks
- Enhance information security awareness among all employees.
Actual and potential, negative and positive impacts
Positive:
- An effective information security management mechanism can enhance information security awareness among all employees and reduce operational losses caused by security incidents.
Negative:
- If the Company's security system is attacked, the information systems and data may be subject to improper use, leakage, tampering, and destruction, which could result in operational risks and hazards.
Action
-
Regularly review information security policies, emergency notifications, incident response, and other related procedures to ensure effective control of residual risks.
-
Reduce network attacks and virus threats, patch antivirus vulnerabilities.
-
Continue information security awareness training, conduct regular refresher training, and strengthen employee information security awareness.
-
Regularly conduct incident response plan drills.
-
Protect confidential business documents.
* This material topic has no actual activities or business relationships involving negative impacts in the current year.
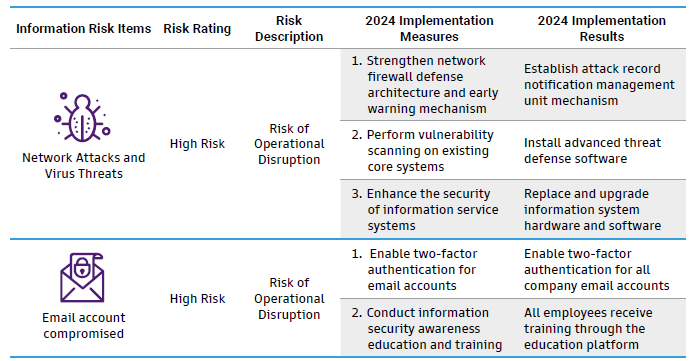
Information Security Risk
To minimize information security risks and prevent confidential information leakage, as well as avoid potential losses from various internal and external information security risks, we have established Information Security Policy and Objectives and Information Security Management Methods in accordance with ISO 27001 and CNS 27001 Information Security Management System standards, to serve as guidelines for implementing information security measures. By developing these policies, we demonstrate leadership's commitment to support information security,establishing an information security management system, and implementing information securityrelated operations within the organization. This also provides guidance for relevant personnel to take appropriate and effective measures that meet the Group's information security requirements,in order to address various information security risks and protect the interests of both internal and external stakeholders of the Group.
Information Security Solutions
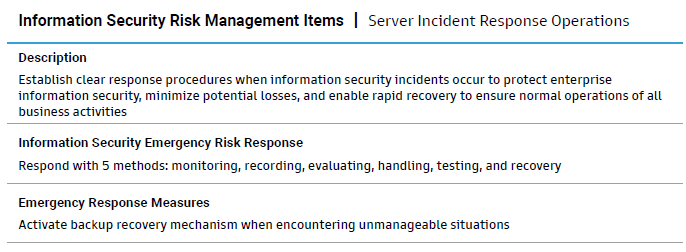
Information security maintenance practices
To comply with information security policies, achieve relevant objectives, establish comprehensive information security protection, the implementation of information security management matters and specific management programs are as follows:
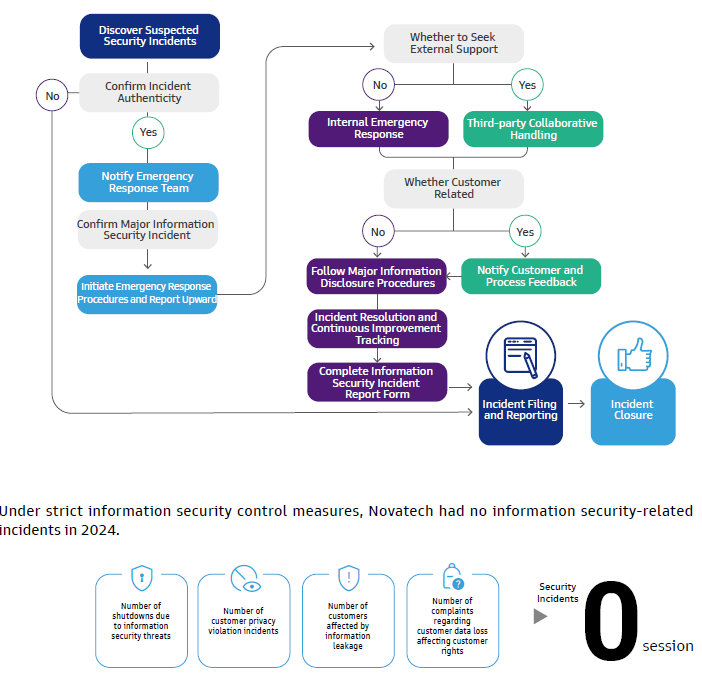
Information Incident Reporting Procedures
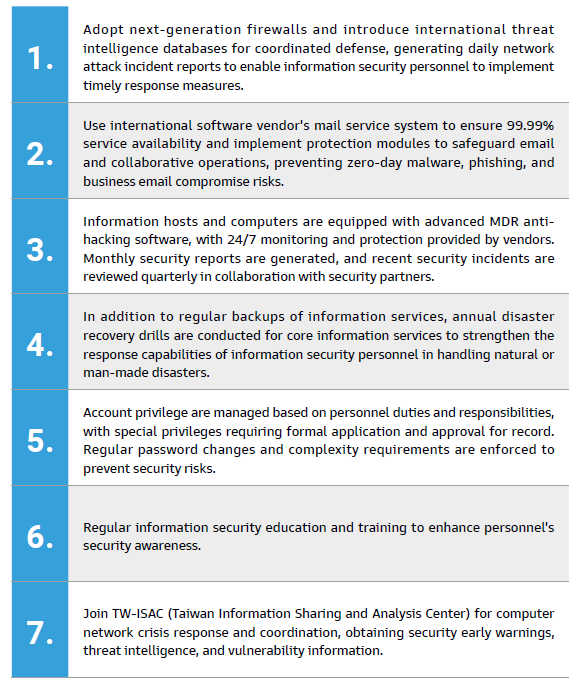
Key Information Security Management Measures
Novatech implements key information security measure on a daily basis ,establishing comprehensive information management mechanisms to ensure thorough
implementation of information security management. Below are our key information security management measures:
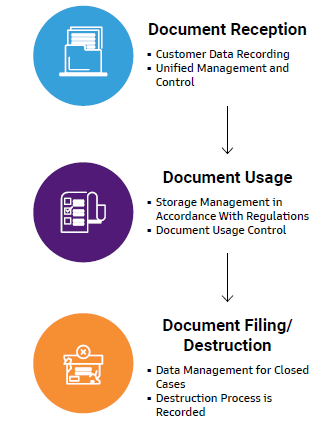
Customer Information Document Control Process
Information Security Health Check
To understand the Company's information security vulnerabilities and prevent security incidents proactively,Novatech has commissioned a third-party security unit to perform information security health checks. For the 2024 inspection items and results, please refer to the following table.
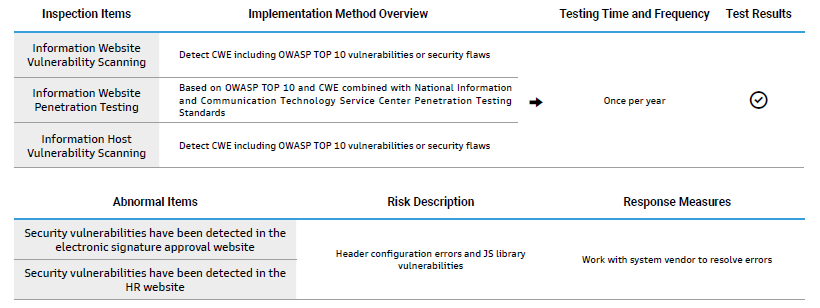
We have made improvements to the above abnormal inspection items and analyzed the causes of anomalies to further implement preventive measures, aiming to reduce the likelihood of security incidents from the source.
Security Drills and Educational Training
Novatech conducts regular security dri lls and educational training to raise employees' information security awareness, strengthening their ability to respond to risk messages, and prevent them from falling victim to security threats.

Information Security Audit
Novatech continues to conduct internal information security audits to drive continuous improvement. Please refer to the following table for internal information security audit results in the past three years (2024-2022).

Information Security Incident Handling
In the event of a security incident, Novatech initiates the following information security incident handling process, with the emergency response team assisting in managing the security incident.